HashiCorp Vault & Boundary – A Powerful Duo for Security & Secrets Management
In the realm of cybersecurity, securing access to sensitive information is paramount. Integrating HashiCorp’s Vault and Boundary offers a powerful solution for managing secrets and accessing infrastructure securely. To make the most of this integration, it’s important to focus on key aspects such as integration, RBAC, dynamic secrets, audit logging, credential rotation, secure communication, high availability, backup and restore, testing and monitoring, as well as documentation and training. By keeping these factors in mind, organizations can enhance their security posture and operational efficiency.
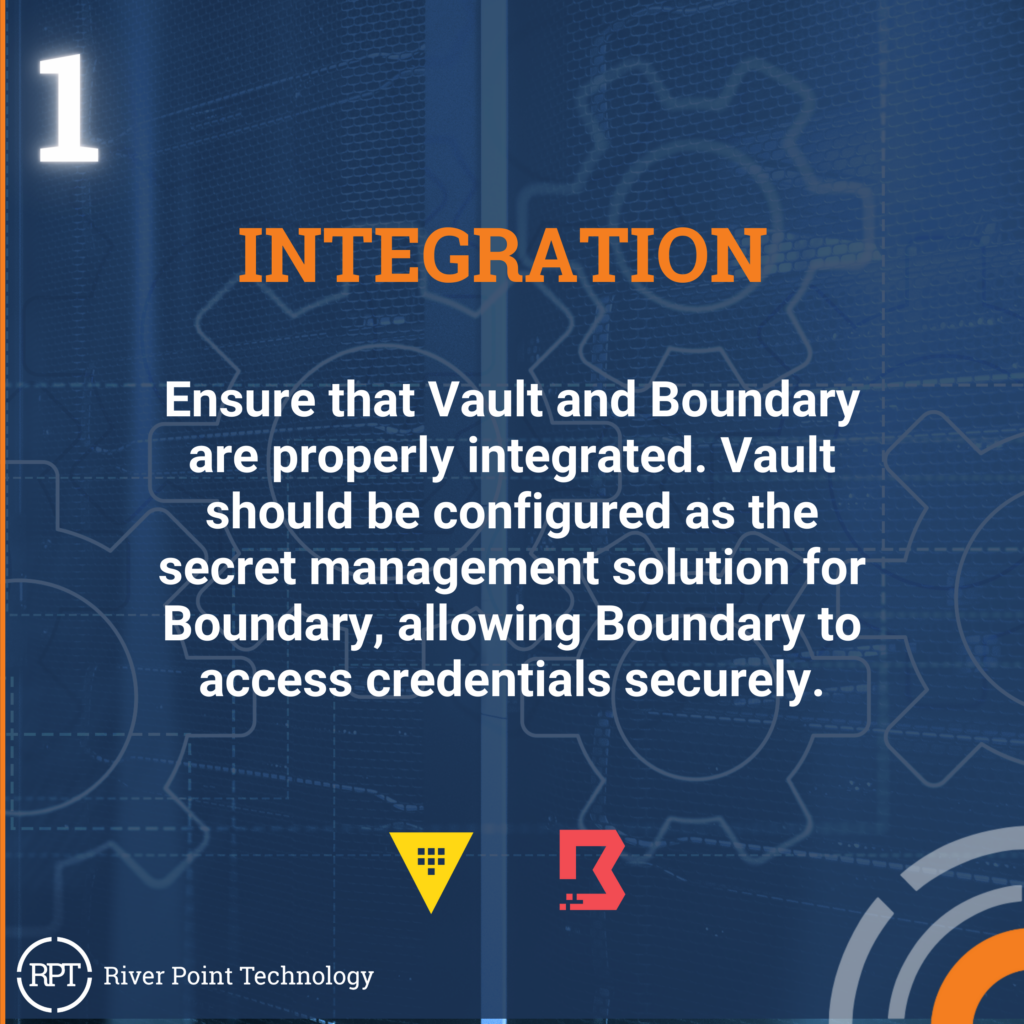
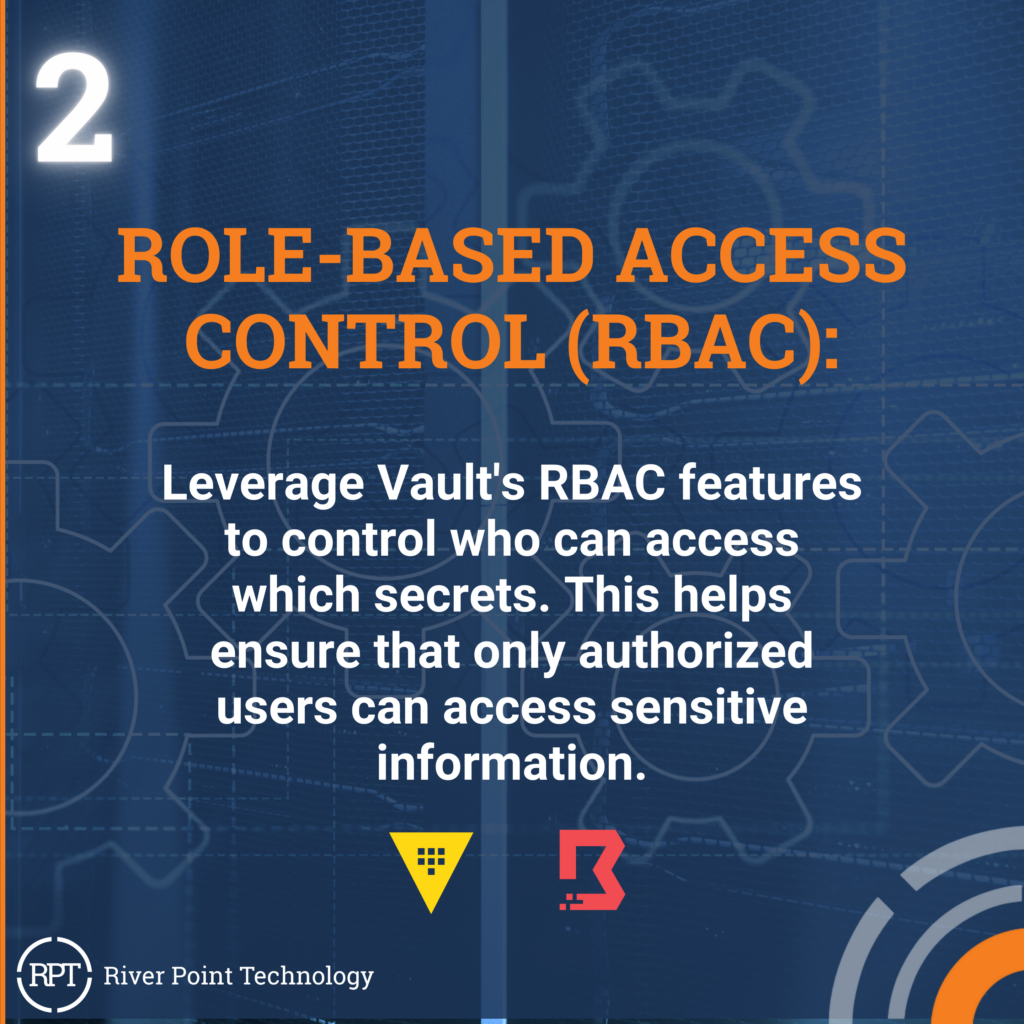
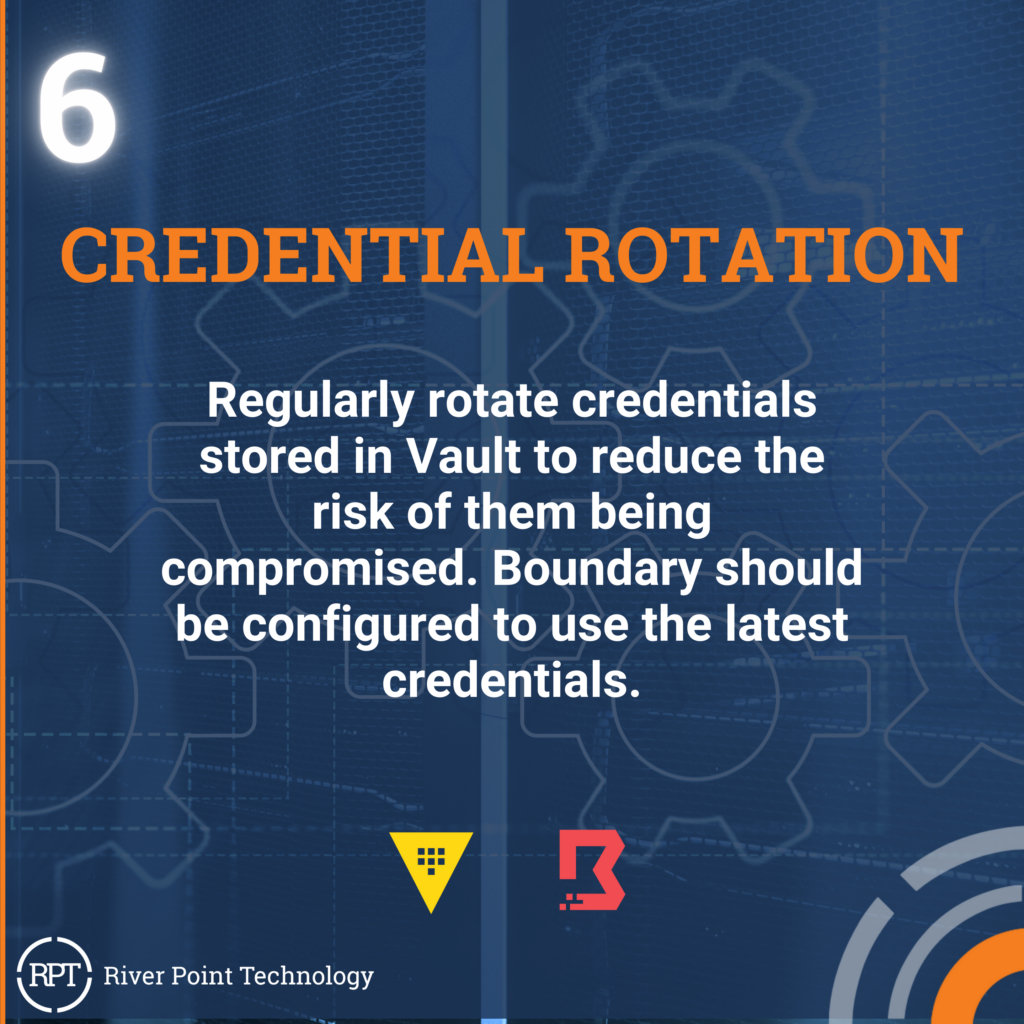
Here are the top ten tips for integration:
Vault and Boundary from HashiCorp are valuable tools for securing and managing access to critical resources. When used together, they form a robust solution for modern infrastructure management. By following the best practices, organizations can effectively leverage Vault and Boundary to enhance security, streamline operations, and ensure compliance. Embracing these best practices goes beyond just protecting sensitive information. It fosters a culture of security awareness within your organization, ultimately improving overall system resilience, reliability, and user experience. With a commitment to best practices, Vault and Boundary can be the cornerstone of a secure and efficient infrastructure management strategy.
Need help maximizing the benefits of using Vault & Boundary? Contact the experts at RPT. As HashiCorp’s 2023 Global Competency of the Year and the only HashiCorp partner with all 3 certifications (Security, Infrastructure, & Networking), you know you’re working the leading HashiCorp services partner. Contact [email protected] today.
About River Point Technology
River Point Technology (RPT) is an award-winning cloud and DevOps service provider that helps Fortune 500 companies accelerate digital transformation and redefine what is possible. Our passionate team of engineers and architects simplify the deployment, integration, and management of emerging technology by delivering state-of-the-art custom solutions. We further position organizations to experience Day 2 success at scale and realize the value of their technology investments by offering best-in-class enablement opportunities. These include the subscription-based RPT Resident Accelerator program that’s designed to help enterprises manage the day-to-day operations of an advanced tech stack, the just-launched RPT Connect App, and our expert-led training classes. Founded in 2011, our unique approach to evaluating and adopting emerging technology is based on our proprietary and proven Value Creation Technology process that empowers IT teams to boldly take strategic risks that result in measurable business impact. What’s your vision? Contact River Point Technology today and see what’s possible.
In the dynamic realm of container orchestration and secrets management, the integration of Kubernetes with HashiCorp Vault stands as a pivotal undertaking, offering enhanced security and streamlined operational workflows. However, this collaboration is not without its complexities, presenting a set of formidable challenges that organizations must navigate. From intricacies in configuration to ensuring seamless communication between these powerful tools, the journey to successfully integrate Kubernetes with HashiCorp Vault demands a strategic approach.
In this exploration, we delve into the top 10 challenges faced in this integration process, shedding light on the key hurdles that organizations encounter and providing insights into overcoming these obstacles for a robust and secure deployment. Here are the top 10 challenges you might face:

Authentication and Authorization: Configuring proper authentication and authorization mechanisms to control access to Vault secrets for both Kubernetes and traditional applications can be challenging.

Secrets Management: Managing secrets across different platforms, ensuring their security, and automating their lifecycle is a fundamental challenge.

Secret Rotation: Implementing automated secret rotation policies and procedures for secrets stored in Vault can be complex, especially for legacy applications that may not support dynamic secret retrieval.

Networking and Security: Establishing secure communication between Kubernetes pods, traditional applications, and Vault while maintaining network segmentation and firewall rules can be tricky.

Integration Complexity: Integrating Vault with a variety of application types, databases, and cloud services, especially when dealing with legacy systems, can lead to integration complexities.

Compliance and Auditing: Meeting compliance requirements and tracking access and usage of secrets for auditing purposes can be challenging, especially in regulated industries.

Secrets Versioning: Managing different versions of secrets, ensuring backward compatibility, and handling secrets rotation gracefully can be complex.

Backup and Disaster Recovery: Developing and testing robust backup and disaster recovery plans for Vault’s data and configurations is crucial to ensure business continuity.

Monitoring and Alerting: Setting up monitoring and alerting solutions to detect and respond to any issues or breaches in real-time is a significant challenge.

Documentation and Training: Ensuring that your team has the necessary skills and knowledge to manage and troubleshoot the integrated environment is an ongoing challenge, as technologies evolve.
Certainly, the real challenges linked to the widespread use of DevOps tools are undeniable. This is why numerous organizations caught in the predicament of managing multiple DevOps platforms are choosing to streamline by consolidating into a central platform. Yet, what does this consolidation involve, and how do you determine the optimal single DevOps platform for migration? Read this Case Study for more answers.