As organizations manage their digital transformation initiatives in today’s business world, their technology investments are often viewed under a microscope. Do they align with strategic objectives? Do they support the company’s innovation goals? Will they pose a business risk? And of course, how cost effective is the investment? Is it a financially responsible choice and what’s the ROI? When it comes to costs associated with protecting an organization’s vital resources, infrastructure, and data, many CTOs, CISOs, and CIOs have to weigh the cost of investment in new technologies vs relying on legacy systems that actually increase their exposure to nefarious actors.
The simple truth is that the typical security methods employed by many enterprises today often come with hidden costs: potential for costly breaches, increased vulnerability, wasted man-hours, and operational inefficiencies. This is where HashiCorp Vault and Boundary come in. When leveraged together they deliver a host of benefits, including cost optimization, streamlined workflows, simplified compliance, and of course they reduce the risk and minimize the financial impact of security incidents.
Understanding the Traditional Cost Conundrum
Before exploring how Vault and Boundary save money, let’s examine the cost burdens associated with traditional security approaches:
- Inefficient Access Management: Manual provisioning and management of passwords, access controls, and VPNs are time-consuming and error-prone, requiring additional IT resources and increasing operational costs.
- Scattered Configurations: Lack of centralized control leads to inconsistencies and vulnerabilities, requiring more resources for monitoring and maintenance, further adding to the expenses.
- Compliance Challenges: Manually handling compliance requirements can be complex and resource-intensive, potentially leading to non-compliance fines and reputational damage, both of which can be financially detrimental.
- Increased Downtime: Security breaches caused by weak access control or outdated methods can result in costly downtime, impacting productivity and revenue.
Cost-Saving Advantages of Vault and Boundary
By integrating Vault and Boundary, organizations can unlock cost-saving benefits without compromising their organization’s security posture:

- Reduced Administrative Burden:
- Automation Powerhouse: Vault automates secrets management tasks like generation, rotation, and revocation, while Boundary automates access control based on pre-defined policies. This frees up IT staff to focus on strategic innovations, reducing labor costs associated with manual processes.
- Centralized Control: Managing secrets and access from a single platform eliminates the need for managing scattered configurations across multiple systems, minimizing administrative overhead and associated fees.
- Enhanced Efficiency and Productivity:
- Streamlined Workflows: Automating tasks and simplifying access control processes improve efficiency for both the IT team and users, saving time and effort that can be directed towards more strategic endeavors.
- Reduced Downtime: By minimizing the attack surface and offering high availability through tools like Vault and Boundary, you can help prevent security breaches and related downtime, saving on costs associated with business disruptions and lost productivity.
- Simplified Compliance Management:

- Built-in Features: Both tools offer features and integrations that help organizations comply with industry standards and regulations, potentially reducing the need for additional tools or external expertise, leading to cost savings.
- Reduced Risk of Non-Compliance Fines: By simplifying and automating compliance efforts, Vault and Boundary can help organizations avoid potential fines and penalties associated with non-compliance, saving significant financial resources.
- Indirect Cost Savings:
- Enhanced Security: By minimizing the attack surface, reducing the impact of breaches, and enforcing least privilege principles, Vault and Boundary can help organizations avoid the financial costs associated with data breaches, including recovery efforts, reputational damage, and potential legal issues.
- Improved User Experience: Secure and streamlined access management can lead to increased user satisfaction and productivity, potentially reducing the need for user support and associated costs.

Long-Term Value Proposition:
While the upfront costs of acquiring and implementing Vault and Boundary should be considered, the opportunity for cost savings over the long term through increased efficiency, reduced downtime, improved security, and simplified compliance makes the investment financially sound.
By implementing HashiCorp Vault and Boundary together, organizations can optimize their financial investment in both platforms. Through automation, centralization, and streamlined workflows, these powerful tools empower organizations to achieve a balance between robust security and financial sustainability, paving the way for an organization to achieve long-term success in the ever-evolving digital world.
Need help maximizing the benefits of using Vault & Boundary? Contact the experts at RPT. As HashiCorp’s 2023 Global Competency of the Year and the only HashiCorp partner with all 3 certifications (Security, Infrastructure, & Networking), you know you’re working the leading HashiCorp services partner. Contact [email protected] today.
About River Point Technology
River Point Technology (RPT) is an award-winning cloud and DevOps service provider that helps Fortune 500 companies accelerate digital transformation and redefine what is possible. Our passionate team of engineers and architects simplify the deployment, integration, and management of emerging technology by delivering state-of-the-art custom solutions. We further position organizations to experience Day 2 success at scale and realize the value of their technology investments by offering best-in-class enablement opportunities. These include the subscription-based RPT Resident Accelerator program that’s designed to help enterprises manage the day-to-day operations of an advanced tech stack, the just-launched RPT Connect App, and our expert-led training classes. Founded in 2011, our unique approach to evaluating and adopting emerging technology is based on our proprietary and proven Value Creation Technology process that empowers IT teams to boldly take strategic risks that result in measurable business impact. What’s your vision? Contact River Point Technology today and see what’s possible.
HashiCorp Vault & Boundary – A Powerful Duo for Security & Secrets Management
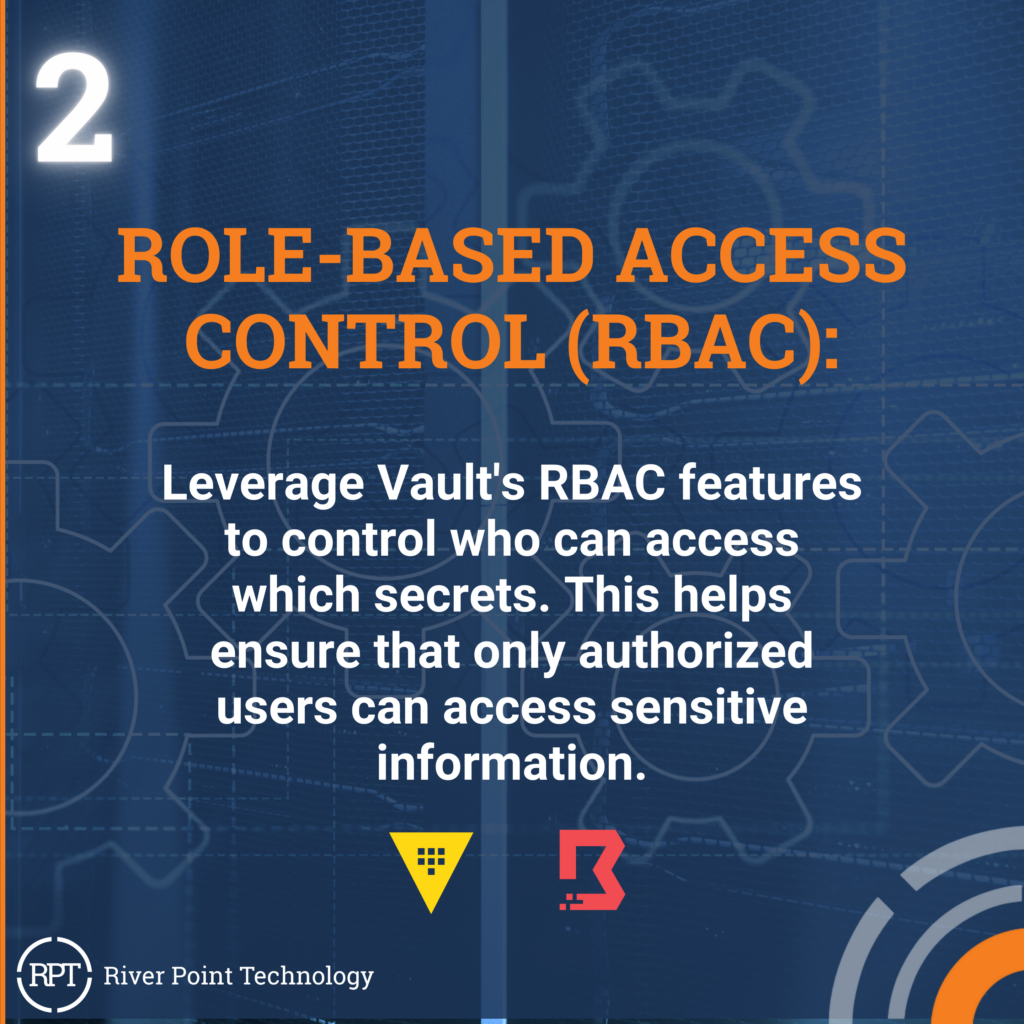
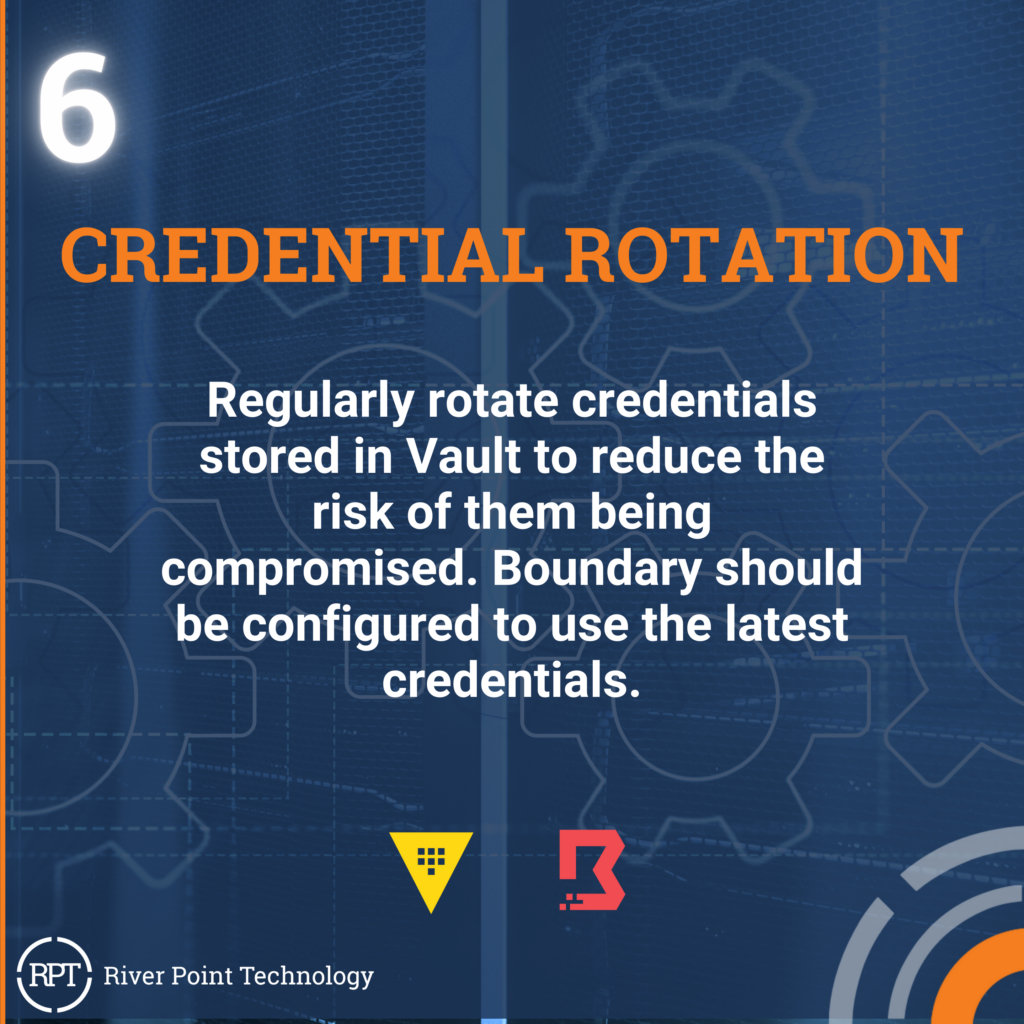
In the realm of cybersecurity, securing access to sensitive information is paramount. Integrating HashiCorp’s Vault and Boundary offers a powerful solution for managing secrets and accessing infrastructure securely. To make the most of this integration, it’s important to focus on key aspects such as integration, RBAC, dynamic secrets, audit logging, credential rotation, secure communication, high availability, backup and restore, testing and monitoring, as well as documentation and training. By keeping these factors in mind, organizations can enhance their security posture and operational efficiency.
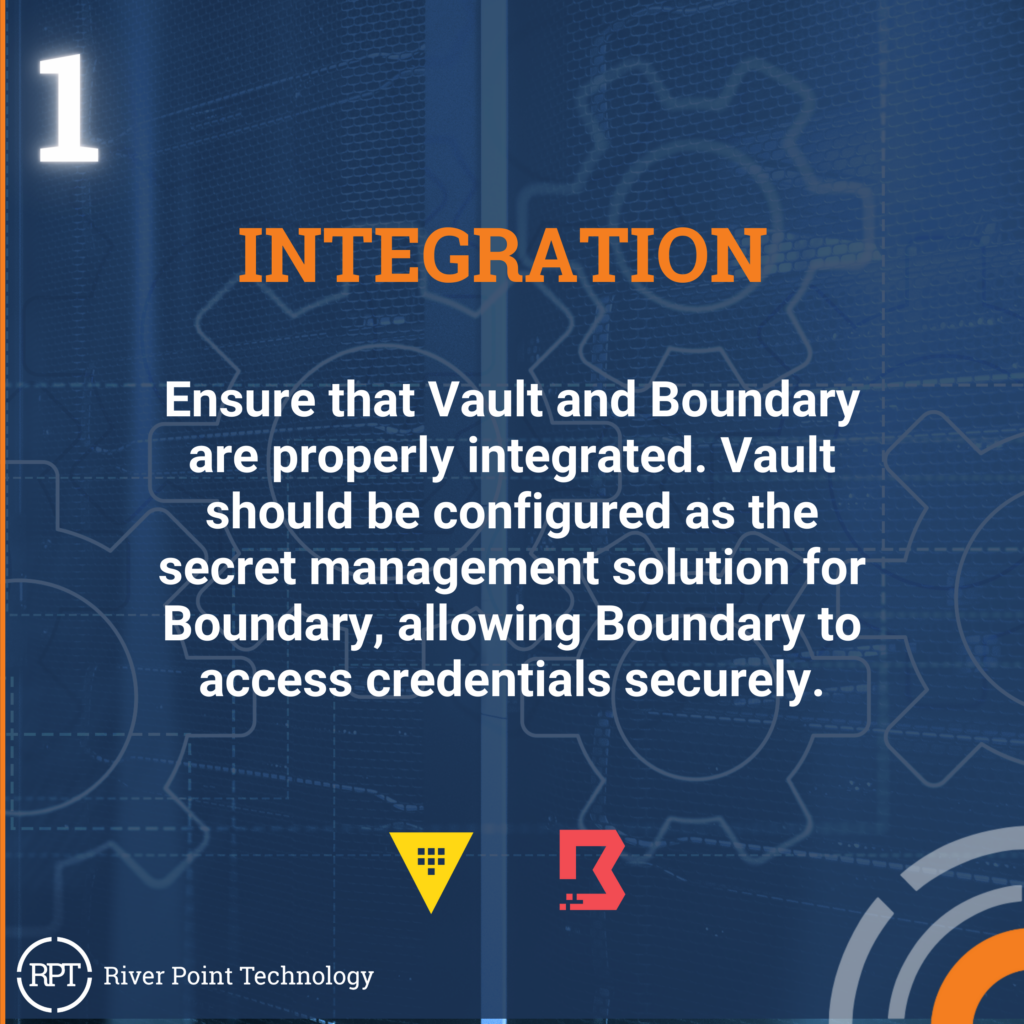
Here are the top ten tips for integration:
Vault and Boundary from HashiCorp are valuable tools for securing and managing access to critical resources. When used together, they form a robust solution for modern infrastructure management. By following the best practices, organizations can effectively leverage Vault and Boundary to enhance security, streamline operations, and ensure compliance. Embracing these best practices goes beyond just protecting sensitive information. It fosters a culture of security awareness within your organization, ultimately improving overall system resilience, reliability, and user experience. With a commitment to best practices, Vault and Boundary can be the cornerstone of a secure and efficient infrastructure management strategy.
Need help maximizing the benefits of using Vault & Boundary? Contact the experts at RPT. As HashiCorp’s 2023 Global Competency of the Year and the only HashiCorp partner with all 3 certifications (Security, Infrastructure, & Networking), you know you’re working the leading HashiCorp services partner. Contact [email protected] today.
About River Point Technology
River Point Technology (RPT) is an award-winning cloud and DevOps service provider that helps Fortune 500 companies accelerate digital transformation and redefine what is possible. Our passionate team of engineers and architects simplify the deployment, integration, and management of emerging technology by delivering state-of-the-art custom solutions. We further position organizations to experience Day 2 success at scale and realize the value of their technology investments by offering best-in-class enablement opportunities. These include the subscription-based RPT Resident Accelerator program that’s designed to help enterprises manage the day-to-day operations of an advanced tech stack, the just-launched RPT Connect App, and our expert-led training classes. Founded in 2011, our unique approach to evaluating and adopting emerging technology is based on our proprietary and proven Value Creation Technology process that empowers IT teams to boldly take strategic risks that result in measurable business impact. What’s your vision? Contact River Point Technology today and see what’s possible.
February 12, 2024 — River Point Technology (RPT), announced today that CRN®, a brand of The Channel Company, has named RPT to its Managed Service Provider (MSP) 500 list in the Elite 150 category for 2024.

The MSP 500 list compiled by CRN serves as a comprehensive guide to identifying and recognizing the top Managed Service Providers (MSPs) in North America. MSPs play a crucial role in supporting businesses by offering managed services that enhance efficiency, simplify IT solutions, and optimize return on investment.
The annual MSP 500 list is divided into three sections: the MSP Pioneer 250, recognizing companies with business models weighted toward managed services and largely focused on the SMB market; the MSP Elite 150, recognizing large, data center-focused MSPs with a strong mix of on- and off-premises services; and the Managed Security 100, recognizing MSPs focused primarily on off-premises and cloud-based security services.
The MSP 500 list aims to showcase and celebrate MSPs that are driving growth and innovation in the industry. These service providers not only enable businesses to harness complex technologies but also contribute to maintaining a strong focus on core business goals without stretching financial resources. By categorizing MSPs based on their business models and areas of expertise, the list helps end-users find the right partners to meet their specific needs and challenges in the rapidly evolving technology landscape.
River Point Technology is a recognized leader in cloud and DevOps services, supporting Fortune 500 companies in accelerating digital transformation and pushing boundaries. Our dedicated team of engineers and architects makes deploying, integrating, and managing new technology easier by providing cutting-edge custom solutions. We also help organizations achieve ongoing success and maximize the value of their technology investments through top-notch enablement programs.
Jennifer Follett, VP of US Content and executive Editor CRN, T he Channel Company, emphasized the significance of managed services for businesses at various scales, stating, “Managed services provide a route for businesses of all sizes to maintain efficiency and adaptability throughout their growth journey. The solution providers featured in our 2024 MSP 500 list are introducing cutting-edge managed services portfolios to the market, enabling their clients to achieve success by optimizing their IT budgets. This allows businesses to allocate resources strategically, concentrating on mission-critical tasks that drive future success.”

“Our core value is driving successful outcomes for our customers, so it is satisfying to see this being acknowledged by our inclusion on the CRN MSP500 list as an Elite 150 partner. I am incredibly proud of our team for their dedication and commitment to being the best in their craft which allows us to bring this value to our customers. We will continue to innovate and humanize technology by leveraging our Value Creation Technology process.” said RPT’s owner and CEO Jeff Eiben.
The MSP 500 list will be featured in the February 2024 issue of CRN and online at www.crn.com/msp500.
About River Point Technology
River Point Technology (RPT) is an award-winning cloud and DevOps service provider that helps Fortune 500 companies accelerate digital transformation and redefine what is possible. Our passionate team of engineers and architects simplify the deployment, integration, and management of emerging technology by delivering state-of-the-art custom solutions. We further position organizations to experience Day 2 success at scale and realize the value of their technology investments by offering best-in-class enablement opportunities. These include the subscription-based RPT Resident Accelerator program that’s designed to help enterprises manage the day-to-day operations of an advanced tech stack, the just-launched RPT Connect App, and our expert-led training classes. Founded in 2011, our unique approach to evaluating and adopting emerging technology is based on our proprietary and proven Value Creation Technology process that empowers IT teams to boldly take strategic risks that result in measurable business impact. What’s your vision? Contact River Point Technology today and see what’s possible.
About The Channel Company
The Channel Company enables breakthrough IT channel performance with our dominant media, engaging events, expert consulting and education, and innovative marketing services and platforms. As the channel catalyst, we connect and empower technology suppliers, solution providers and end users. Backed by more than 40 years of unequalled channel experience, we draw from our deep knowledge to envision innovative new solutions for ever-evolving challenges in the technology marketplace. www.thechannelco.com
Follow The Channel Company: Twitter, LinkedIn, and Facebook.
© 2024 The Channel Company LLC. CRN is a registered trademark of The Channel Company, LLC. All rights reserved.
The Channel Company Contact:
Kristin DaSilva
The Channel Company